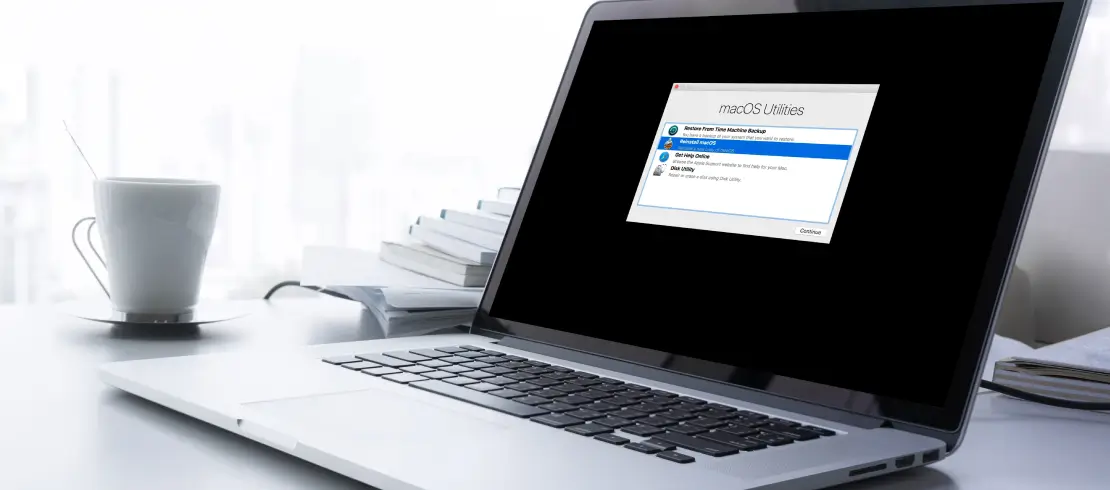
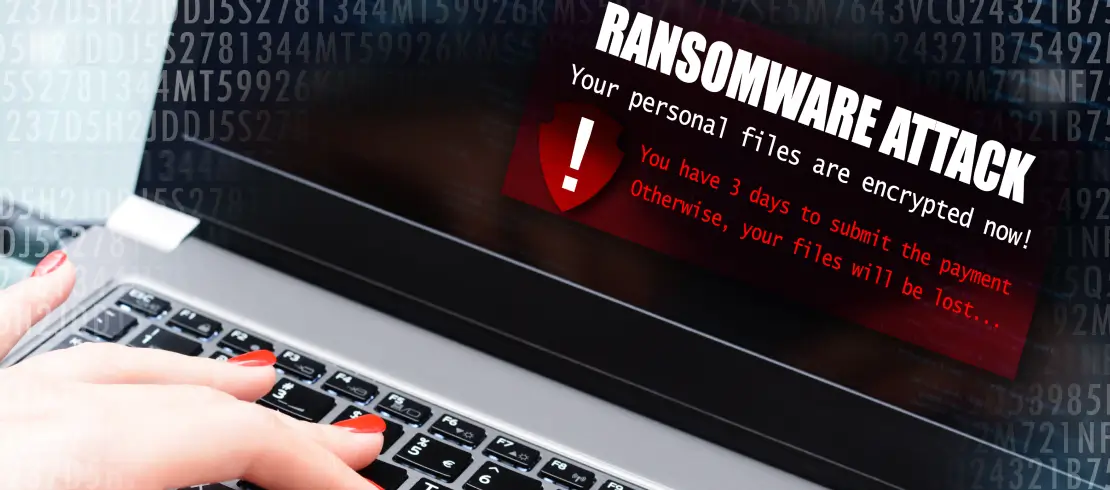
Welcome to our blog! Here we cover many topics connected to data recovery, digital security and more. Our goal is to offer guidance and insightful analysis for people at any ability level. We provide thorough tutorials on data recovery with discussions of the typical causes of data loss, detailed instructions for restoring lost or corrupted data, and advice on how to stop future problems. Join us to keep up with the newest industry trends and innovations.