When WRAL in Raleigh, North Carolina discovered that their six-drive RAID 5 went offline, their news team knew that raw footage needed to be recovered. They decided to call the experts at Secure Data Recovery to retrieve the lost files. Despite the logical damage, our engineers repaired the RAID and returned over 20,000 video files to WRAL.
An Overview of RAID 5
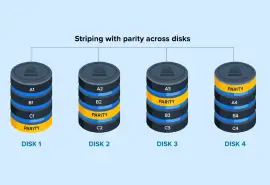
RAID is a storage method that improves device performance while offering a degree of fault tolerance to users. RAID stands for a redundant array of independent disks. The technology integrates multiple hard disks into a single logical, then distributes data across drives in the array. The number refers to the RAID’s configuration.
In this case, WRAL had a Promise Pegasus R6 in a RAID 5 configuration. A RAID 5 is configured to divide data into smaller portions. These blocks of data are spread across the drives through a process called striping. Striping disperses data in a specific pattern. For example, the first block of data might be saved to Disk A while the second chunk could be sent to Disk B. The pattern continues until each block is distributed across the six disks. Striping splits the workload between multiple drives, improving overall read and write speeds.
But recovering data from a failed RAID can be complex.
Diagnosing Data Loss and Developing Custom Solutions
WRAL sent their RAID 5 to us for evaluation. Our technicians determined that the RAID configuration was lost, meaning the parameters that managed its operation were no longer accessible. As a result, the RAID controller cannot recognize how data was distributed across the disks.
In that situation, professionals must rebuild the RAID configuration. To start, all disks in the RAID are imaged. Imaging creates a bit-for-bit replica of the stored data. Engineers work with the image during recoveries to preserve the existing data.
Once imaged, we used specialized tools and techniques to repair the RAID. That involved destriping all data from the damaged RAID. To destripe, an advanced algorithm reads available data and calculates missing information through a series of reversible operations. After piecing together the file structures, we reconstructed the original architecture.
When the RAID was restored to a functional condition, we developed custom utilities to extract the inaccessible files. However, we encountered significant corruption. Our team performed manual file repair until working data could be delivered to WRAL.
In the end, we recovered their entire archive.
“Secure Data Recovery worked around the clock to reunite us with our footage,” said engineering supervisor Josh Knapp. “They earned their reputation as data recovery experts.”
Professional RAID Data Recovery
Since 2007, Secure Data Recovery has pushed the boundaries of what is possible. It is the reason we accept cases that other companies cannot or will not recover. Nevertheless, we maintain a 96% success rate. No matter the circumstance, we will exhaust every technological option. That’s why we have resolved over 100,000 cases and retrieved billions of lost files.
Our RAID data recovery services are no different. We have made complicated recoveries for government agencies, corporations, small businesses, and individuals. In each instance, we drew on our extensive experience and understanding of all failure scenarios and models, including hundreds of recoveries featuring Pegasus storage.
In addition, we have the expertise to provide innovative solutions to unique challenges, whether it is raw footage from a local television station or something important to you.
Call us at 800-388-1266 for a free consultation.