Engineers at Secure Data Recovery handle devices storing extremely sensitive data every day. We take the duty to protect personal and private data very seriously. Our audited process demonstrates our commitment to your privacy and security.
However, many parties do not share the same commitment. That makes it essential to learn how to dispose of hard drives. Especially for businesses and people looking to sell their old hard drives for donor parts or repurpose them.
To prove the dangers of unsanitized hard drives, we decided to conduct a simple experiment.
How much data could our engineers recover from hard disk drives (HDDs) that claimed to be sanitized?
The results might surprise you. And may lead you to reconsider IT strategies for end-of-life drives.
Key Findings:
- Only 30.7% of hard drives were properly sanitized by sellers.
- We recovered over 6 million files from 42 hard drives in the sample.
- Recovered file types included images, videos, documents, audio, mailboxes, and more.
- Our team encountered 37 disks with physical damage or encryption, but estimated that data was recoverable in most cases.
What Is Data Destruction?
Data destruction is the process of permanently purging data from a storage device to ensure confidential information is protected.
The practice aims to remove data from a storage medium before it falls into the wrong hands. Globally, the average cost of a data breach was $4.4 million in 2025. Substantial fines are also possible for mishandling data in regulated industries. Some victims never fully recover from data theft. Those facts highlight the importance of secure data destruction. Otherwise, an old hard drive could become an expensive mistake.
Yet many small businesses and individuals still neglect to destroy data on discarded disks.
Data Destruction and Disposition Failures
Here is what we discovered about supposedly sanitized hard drives, and the potential consequences of data destruction and disposition failures:
Our Experiment
We purchased hard drives being sold online in two batches. In total, we bought 114 hard drives from different sellers. They cost less than $10 on average. The disks were listed as sanitized. Sellers described their condition as refurbished, used, dead, or for parts. All models were produced between 1994 and 2022.
From the onset, our team chose not to repair damaged hard drives or retrieve encrypted files in the sample. We made this decision given the cost of donor parts and the value of time.
We verified that the recovered files were intact but never viewed their contents.
Our technicians destroyed all recovered data after the experiment.
The Results
| Sample Hard Drives (Purchased Online) | |
|---|---|
| Unsanitized | 42 |
| Damaged or Encrypted | 37 |
| Sanitized | 35 |
| Total | 114 |
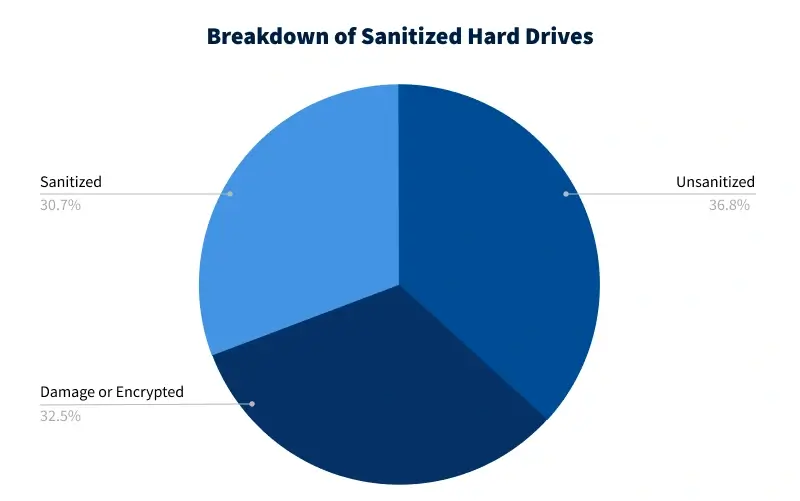
Sellers successfully sanitized only 30.7% of the hard drives in the sample. Purging data from the magnetic platters prevented up to 64 TB of data from being exposed.
A surprising 36.8% of the purchased disks contained recoverable data. Those hard drives yielded a total of 6,002,530 files.
| Recovered Files From Unsanitized Hard Drives | |
| Image Files | 3,980,371 |
| Document Files | 305,256 |
| Video Files | 287,208 |
| Mailbox Files | 204,355 |
| Audio Files | 159,676 |
| Miscellaneous Files | 1,065,664 |
| Total | 6,002,530 |
We sorted the recovered data into six categories: image, document, video, mailbox, audio, and miscellaneous files.
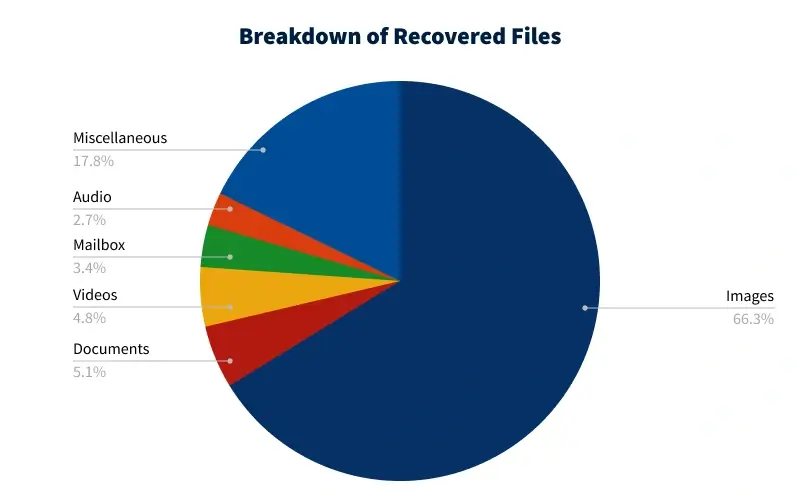
Images accounted for 3,980,371 recovered files. Popular file formats included GIF, PNG, and JPEG. These files were likely photos of family and friends, memes that someone saved, or web assets.
We retrieved 287,208 video files from the hard drives. Typical extensions were AVI, FLV, and MP4. AVI files bundle audio and video into a single container. They are quite common in software development. FLV files are a container format for Adobe Flash Player. MP4 is the standard file type for most videos due to its balance of quality and size, as well as its cross-platform support. The files could cover the full spectrum, from how-to guides and YouTube videos to major moments or special events.
There were 159,676 audio files on the disks. The vast majority were MP3s. MP3 is a very popular file format for downloaded songs.
In most cases, the above file types would not inflict much damage if stolen.
Document, mailbox, and miscellaneous files could be a different story.
Our experts recovered 305,256 documents from the unsanitized drives. Examples included Word, Excel, PowerPoint, and PDF files. These documents could expose confidential reports, intellectual property, financial statements, personally identifiable information, and more. Any leaks could reveal sensitive data or strain public trust.
We recovered 204,355 files from mailbox databases. A mailbox database archives emails, attachments, contacts, and calendar items for users on a server. Bad actors could glean insights from the data and use it to defraud the business or impersonate an insider.
The batch contained 1,065,664 miscellaneous files. It was the second-largest category on the disks. We defined them as unique databases, proprietary formats, and system files like credentials, logs, scripts, services, and settings. An advanced group can use this data to understand what happens within an app or system. They could weaponize that knowledge for financial gain.
Finally, the sample had 37 hard drives with varying levels of physical damage or encryption. As mentioned, we chose not to attempt to recover data from these devices. However, the condition of many hard drives in this subset suggested that data recovery was feasible.
What We Learned
In short, not enough parties take the sanitization process seriously.
Sellers claimed to sanitize the hard drives in their listing. Yet, our data recovery experts managed to extract over 6 million files from the disks. While we wiped all files after the exercise, the risk of exposing personal data or private information to the public remains. And each oversight could have disastrous consequences.
Physical destruction is the surest way to remove data from a storage device. However, destroying a hard drive prevents IT teams and people from selling old hardware to cover replacement costs.
NIST guidelines explain the most effective techniques for purging data from hard drives. Following these strategies before sending the disk to a buyer or recycler can safeguard valuable data.
The bottom line: You can never be too careful when sanitizing media that once stored your critical data.
Secure Data Destruction Services

Our certified data recovery services prove that we know how to recover data from hard drives. We also know how to dispose of hard drives, so no one else can recover data from their platters. When finished, we issue a certificate of destruction to confirm the hard drive disposal was successful. This document provides our customers with the peace of mind that their data is permanently gone.
Call 800-388-1266 or request help to learn more about our range of secure data destruction services.








